I recently found myself in a situation where I wanted to have a small WiFi access point allowing me to route all the Internet traffic through a VPN with a kill-switch, and decent performance. As I had an unused Raspberry Pi, I decided to make use of it with OpenWrt to achieve my goal. In this article, I will document the procedure to have everything properly configured. The instructions are valid for OpenWrt 21.02.3.
Getting OpenWRT Running#
The first step is to flash OpenWRT into a microSD card. Raspberry has software to do so, but you can also use dd, or whatever software you are comfortable with. The image can be found on OpenWrt’s website.
Once this is done, you can plug your Raspberry Pi and your computer into a switch, and boot the machine. You will then be able to access the LuCI interface at 192.168.1.1 and to log in as root with no password.
Note that by default, your microSD card will only be formatted with partitions of a few hundred MBs, so at some point, you might want to reformat your partitions if you want to go into advanced use of OpenWrt.The various instructions on the Internet did not work for me, and I had no time or need to investigate further, but I’ll leave references at the end of the article.
Once we access the administration interface, we first want to go to System/Administration and set a decent password. I also recommend changing the SSH settings to only allow logging in with an SSH Key.
Basic Network Configuration#
Now that OpenWrt is up and running, we want to enable the Wifi and do some basic network configuration.
In Network/Wireless, edit the wireless network interface:
- You can choose the frequency that suits your needs best. I used
Nmode with a5 GHzband and an automatic channel. If you want to set things manually, you can use theChannel Analysisin theStatusmenu - Mode:
Access Point - Network:
lan - Encryption: anything that is
WPA2orWPA3,autocipher, and a strong key - In the advanced settings, there is also an option to prevent client-to-client communications
Then, enable the interface, and you should see your WiFi network. You might notice that you can add an extra WiFi AP in the radio0 configuration. Doing so will only make OpenWRT unhappy, and your changes will be automatically un-applied.
The final step before being able to use the WiFi is to configure the interfaces in Network/Interfaces. By default, you should have a single Interface br-lan, or something of the kind. We will edit this interface to have the following:
- Protocol:
Static address - Device
wlan0 Bring up bootchecked- IPV4 address
192.168.1.1 - Netmask:
255.255.255.0 - Firewall-zone:
lan - Make sure that the DHCP service is not disabled
Then, we will add an interface for eth0 with the following settings:
- Protocol
DHCP Client - Device
eth0 Bring up on bootenabled- Firewall zone:
wan
When all of this is done, the final step before being able to use the WiFi to access the Internet is to check the firewall settings in Network/Firewall. You should have two zones:
lan => wanshould havelanas aCovered networks, allow forward to thewandestination, and haveInput,Output, andForwardas acceptedwan => DROPshould haveeth0asCovered networks,dropInputandForward, andacceptOutput
You can now click on Save & Apply, and connect to your WiFi.
Configuring the VPN#
Basic Configuration#
In the final step of this walkthrough, we will use ProtonVPN with OpenVPN, but you can use pretty much any provider, and other protocols such as WireGuard are also usable.
First, we need to install some packages. Go to System/Software, update the lists if nothing pops up in the available packages, and install openvpn-openssl and luci-app-openvpn. Refresh your UI, and you should see a menu VPN/OpenVPN.
We will then use the OVPN configuration file upload, and give it the configuration file provided by ProtonVPN. The configuration will then appear in the list of OpenVPN instances, and we will edit it. You should add the path of the auth-user-pass file in the top text field, and put your username/password in the second one.
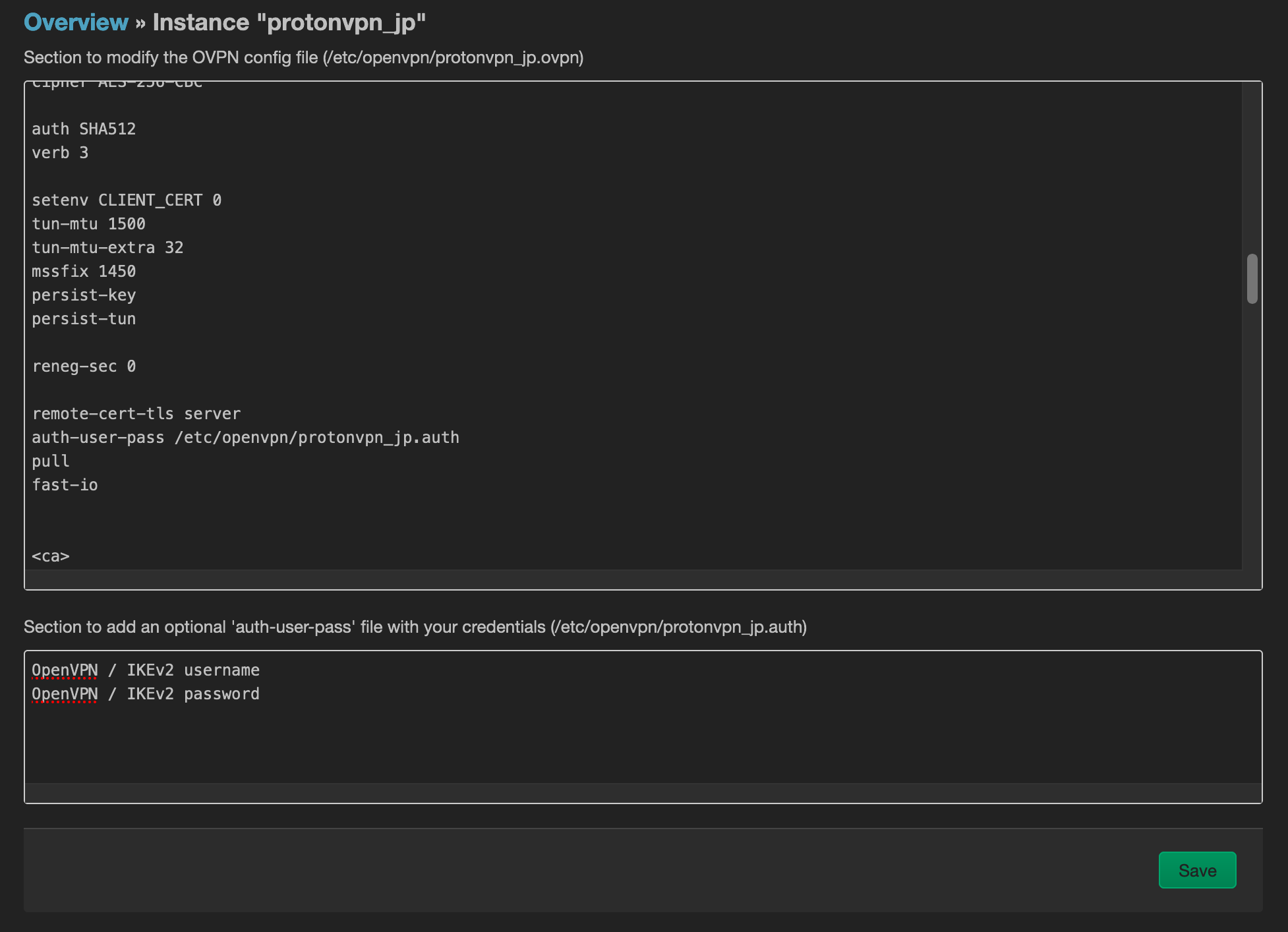
Once this is done, you can go back to the list of instances, check the Enabled checkbox, and Save & Apply. At this point, the screen should show the VPN as started.
Then, we will configure a new interface for the VPN. In Network/Interface, add a new Interface tun0, with protocol as Unmanaged, Bring up on boot, and tun0 as the device. In Firewall Settings, create a firewall-zone VPN. We will then configure this zone in Network/Firewall with the same settings as wan => DROP, with the difference that we will use lan in Allow forward from source zones, and accept the Forward. We will also go to the lan => VPN zone, and add the VPN zone in the Allow Forward. You should now have the following:
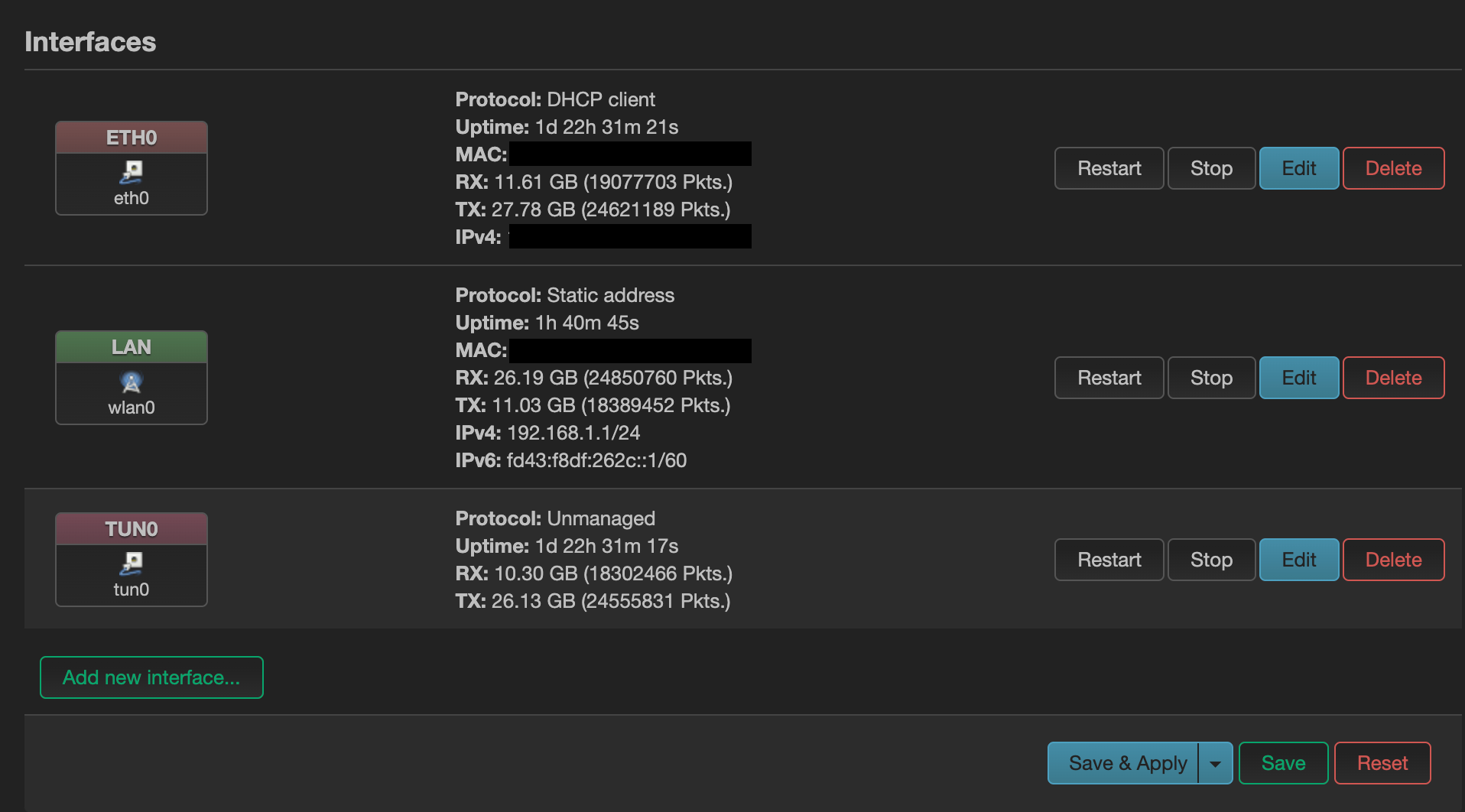
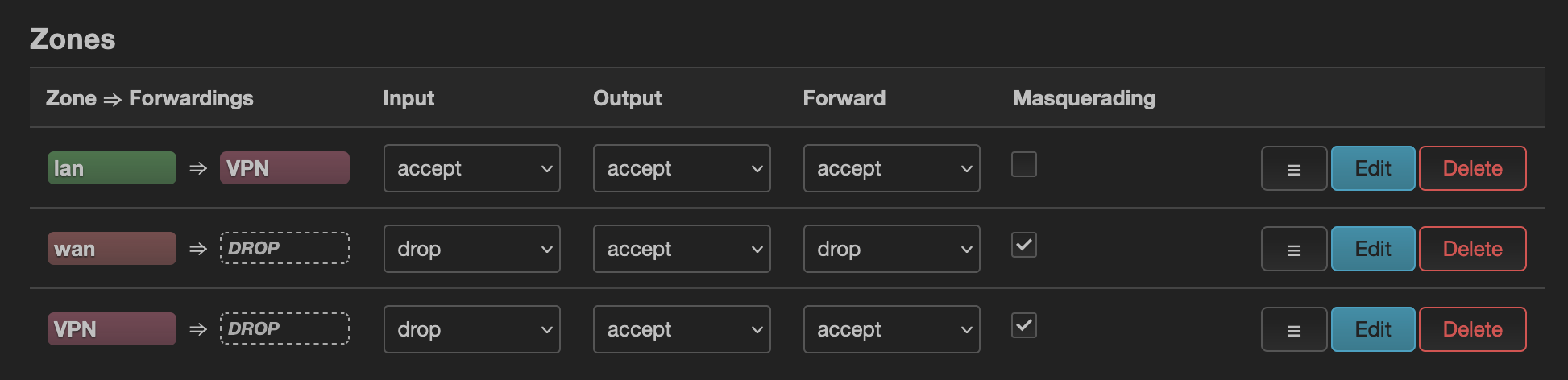
Now, the connection will go through the VPN if it is on, but will still be able to reach the Internet if the VPN is down. One final thing that we want to do to avoid DNS leaks is to use custom DNS servers with the eth0 interface, and to disable the option Use DNS servers advertised by peer.
Kill Switch#
If you want to configure a ‘kill switch’ for the VPN (i.e., stop allowing Internet traffic to go through if the VPN is down), you can do that easily by changing the lan => VPN zone in the firewall configuration. You only have to remove lan from the Allow forward to destination zones.
If you have multiple WiFi networks at home, you need to configure your machines to only auto-connect to your OpenWrt network. Otherwise, they might connect to another WiFi, and you will connect to the Internet without VPN.
Disable VPN for a Device#
If you are not using the kill-switch, and want to have a device connect to the Internet without using the VPN, you can install the package vpnbypass, set your device to have a static DHCP lease in the landing page of OpenWRT, and add a Local IP Address to Bypass in VPN/VPN Bypass.
To Go Further#
Now, you have a router allowing all the connected devices to access the Internet via VPN, but there are still some things that you can improve in the configuration. For example:
- There is a
snortpackage that you could install to improve the security of your network - You could connect an external WiFi AP, and make it so that devices connected to this AP can access the Internet without VPN, for example, if you want to use Netflix (I’m sure that you can do that with a single AP by playing with the firewall rules, but I personally like simplicity)
- Install an adblock package and configure it so that all the connected devices can also have the benefit of no ads (e.g. if you have iOS-based devices, there is no possibility to install adblock extensions in the browser)
References and Credits#
References#
- OpenWrt routers and Mullvad VPN (Proton VPN)
- How to set up ProtonVPN on OpenWRT routers (Mullvad VPN)
- OpenVPN client using LuCI (OpenWrt)
- OpenWrt on x86 hardware (PC / VM / server) (OpenWrt)
Resources Change Partitions#
- https://forum.openwrt.org/t/expanding-openwrt-squashfs-image-sdcard/60606/7
- https://forum.openwrt.org/t/how-to-expand-the-space-of-overlay/74093
- https://openwrt.org/docs/guide-user/additional-software/extroot_configuration
- https://java-in-cloud.blogspot.com/2016/08/openwrt-extroot-and-multiple.html
- https://moreless.medium.com/extend-partition-and-file-system-on-raspberr-a48af9e90858
- https://linuxconfig.org/how-to-extend-lede-openwrt-system-storage-with-an-usb-device
- https://linuxconfig.org/how-to-create-loop-devices-on-linux
Credits#
- Cover photo by Jainath Ponnala on Unsplash